

Investigation by Selwyn Manning.
THE PRIME MINISTER JOHN KEY’s admission on Wednesday that whistleblower Edward Snowden “may well be right” that our data-communications may be accessible through XKeyscore raises further questions of whether John Key has been telling the ‘whole truth’, whether he has lied, or whether he is simply out of his depth.
The New Zealand Herald today reported:
Prime Minister John Key acknowledged today that NSA whistleblower Edward Snowden’s claim that New Zealanders’ data is accessible through the controversial XKeyscore system “may well be right”.
However, he maintained that information will not have been gathered under any Government Communications Security Bureau (GCSB) mass surveillance programme as the agency doesn’t have that capability. (Ref. NZHerald).
Has the Prime Minister been outplayed by the deep state, the true masters of the great game? If so, he wouldn’t be the first.
Whatever the truth is, with only a few days left before Polling Day, the Prime Minister’s comment drives home the need for New Zealanders to fast become familiar with what the United States-based spy agency does, its reach around the world, how it sets up sites in countries like ours, and most importantly what the National Security Agency (NSA), has already admitted to.
Once armed with that information, it is up to us all to exercise our view of this matter by exercising our vote on Saturday.
Firstly, while many are seeking clarity on whether the NSA has a facility in New Zealand, we must realise that the agency has many difference faces.
Let’s consider: how does the NSA operate? How does it use privately owned businesses, corporations, to do its work abroad? How does it partner up with such players to construct what is simply a spy network of privately owned profitable cells and government agencies all feeding back to the mothership Stateside? Is this the ultimate version of a public-private-partnership (PPP)? And, is this how it masks, in part, its operation around the globe?
The NSA’s PPP arrangements permit the state-aligned entity to avoid laws, regulations and statutory controls on what it, and other Five Eyes members like the GCSB, can and cannot do.
Companies like Palantir International, conceived deep within California’s Silicon Valley, has become a giant among the technology companies that have made millions and millions of dollars networking with governments and the world’s largest spy agencies – the Central Intelligence Agency (CIA) and the NSA among them.
Palantir Technologies New Zealand Ltd is operating in New Zealand. Now, we do not at this juncture suggest Palantir is operating in New Zealand at the behest of the NSA, but we can confirm that it registered as a company here in 2012, its official office is listed in the Government companies office register as being with legal firm Simpson Grierson, 88 Shortland St, Auckland; that it has a headquarters in Wellington; it recruited for interns at Victoria University as recently as May 19 this year; it actively employed data analysis and computer engineers at locations in New Zealand, has invested around $12 million into New Zealand information communication technology (ICT) start-ups, and certainly specialises in highly efficient deep data analysis on a global-scale.
Palantir states on the New Zealand section of its global corporate website: “We are composed of technical people doing technical work, software engineers who establish natural rapport before discussing solutions and pounding the keyboard, analysts who can tweak servers, and communicators who listen. Our goal is to implement our platform where people need it, without a surplus of jargon. We don’t do business as usual; we do business as Palantir.”
So what is this business it speaks of?
Well the Wall Street Journal describes one of its products, Palantir Gotham, as: Palantir Gotham is used by counter-terrorism analysts at offices in the United States Intelligence Community and United States Department of Defense, fraud investigators at the Recovery Accountability and Transparency Board, and cyber analysts at Information Warfare Monitor (responsible for the GhostNet [a Chinese cyber attack network] and the Shadow Network investigation). Palantir Metropolis is used by hedge funds, banks, and financial services firms. (Ref. WSJ).
WSJ wrote in the early stages of Palantir’s rise:
Palantir’s software has helped root out terrorist financing networks, revealed new trends in roadside bomb attacks, and uncovered details of Syrian suicide bombing networks in Iraq, according to current and former U.S. officials familiar with the events. It has also foiled a Pakistani suicide bombing plot on Western targets and discovered a spy infiltration of an allied government. It is now being used by the Central Intelligence Agency, the Pentagon and the Federal Bureau of Investigation. Yet Palantir — which takes its name from the “seeing stones” in the “Lord of the Rings” series — remains an outlier among government security contractors.
Only yesterday (September 15, 2014 US timezone) Palantir was cited in the Silicon Valley Business Journal as adding US$50 million to its corporate spy war-chest.
Palantir Technologies disclosed on Friday that it has raised $50 million more in a funding round that now totals about $444 million. The secretive Palo Alto Big Data analytics company led by Alex Karp didn’t disclose where the funding came from in its filing with the Securities and Exchange Commission. The company was already one of the most heavily funded startups in Silicon Valley. It raised a total of $829 million before this latest funding. (Ref. SVBJ).
The report noted: Palantir’s backers include the CIA’s In-Q-Tel venture fund and, the company’s co-founder Peter Thiel’s Founders Fund.
The report listed among its customer’s the US “government intelligence agencies such as the National Security Agency”.
All of this material is easily accessed via the internet.
It would be helpful if New Zealand’s Prime Minister John Key revealed what exactly Palantir Technologies New Zealand Ltd is doing here, particularly as the company states in its recruitment material that it is working with government to deploy its platform.
What platform is this? Why is this company so intent on establishing itself here?
It would also be worthwhile for all those interested in investigating Edward Snowden’s claim – that the NSA has operations in at least two locations, one in Auckland (perhaps located near the Southern Cross cable underground hub on Auckland’s North Shore, that feeds large capacity to the Albany IT sector) and another north of the city – to consider the PPP tactic.
Companies like Palantir have the expertise and the track-record of getting results for their clients
For example, Palantir’s corporate website states: “DATA FUSION PLATFORMS Back-end infrastructure for integrating, managing, and securing data of any kind, from any source, at massive scale.” (Ref. Palantir.com).
In 2012, shortly after it established in New Zealand, Palantir was actively recruiting for IT specialists. For example:
Palantir is looking for a brilliant, technical mind to help deploy our Government platform in New Zealand. We need someone to take a step back, look at who we are interacting with, and what those interactions mean across the organisation.
It offered insight into what it does, stating: We currently offer a suite of software applications for integrating, visualizing and analyzing the world’s information. We support many kinds of data including structured, unstructured, relational, temporal and geospatial. (Ref. LinkedIn).
Describing its operation, Palantir wrote it is: “broadly deployed in the intelligence, defense, law enforcement and financial communities, and are spreading rapidly by word of mouth into applications in other industries and realms of impact.”
Palantir clearly has an overt presence here in New Zealand. And nothing suggests its operation is anything other than lawful. The above references are cited in the public interest simply to illustrate how state spy agencies contract and outsource to the private/corporate sector, and how the private/corporate sector accumulates vast profits in what is a very lucrative field.
WHAT WE DO KNOW:
What we do know is contained within a cache of significant information sourced from the NSA itself – made public thanks to Edward Snowden and investigative reporter Glenn Greenwald.
The NSA’s own documents show that over the past five years the NSA has developed vast networks of “partnerships” with the corporate sector.
Let’s consider a sample.
Identified as Fairview, the NSA has developed what it states as: Key corporate partner[s] with access to international cables, routers, and switches.
It describes a US-based arrangement an example:
“The partner operates in the U.S. But has access to information that transits the nation and through its corporate relationships provide unique access to other telecoms and ISPs. Aggressively involved in shaping traffic to run signals of interest past our monitors.” (Ref. NoPlaceToHide Greenwald/Snowden doc: Page 104. US-990 Fairview).
The NSA goes on to describe how it used corporate elements to help mask its operations. The documents show how the sensor sites around the world are not necessarily run by the NSA, nor does it have a sign above the data-centre door heralding ‘This is the collection office of the NSA’. Rather, the sensor sites appear to be a mix of state owned infrastructure, and privately owned enterprise. But let’s be clear: the NSA is the benefactor of the data that is collected… the recipient of your communications, and can use it as it wishes, whether the acquiring of the data is legal or not.
For example: STORMBREW.
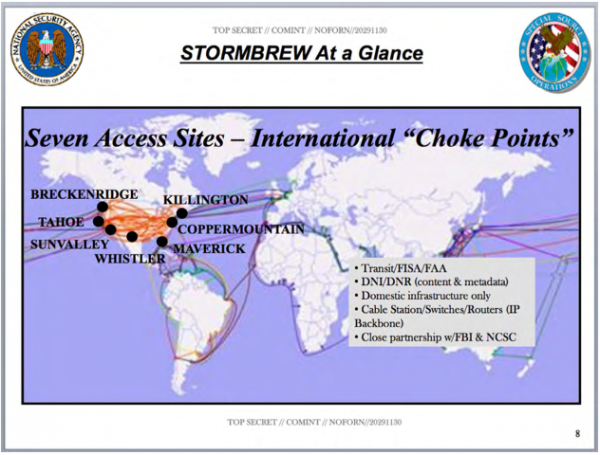
STORMBREW: Location, Auckland, NZ. (Ref. NoPlaceToHide Greenwald/Snowden doc: Page 107).
-
The jargon: DNI/DNR = CONTENT AND METADATA; DOMESTIC INFRASTRUCTURE ONLY; CABLE STATION/SWITCHES/ROUTERS/IP BACKBONE); CLOSE PARTNERSHIP WITH FBI & NCSC.
The UPSTREAM element of STORMBREW is described by the NSA as a “collection of communications on fiber cables and infrastructure as data flows past” and is used by the following platforms that are specific to regions around the world: Fairview, Stormbrew, Blarney, Oakstar).
Understanding the protocol references is also vital when we attempt to understand what is being done in our name.
DNI and DRN are important distinctly different references.
-
DNI Selectors = 9 US based service providers (PRISM). Worldwide sources (UPSTREAM).
DNR Selectors = Worldwide sources.
Both DNI and DNR provide realtime collection (surveillance), while PRISM also provides access to stored communications available via search within the PRISM platform. Both DNI and DNR provide access to VOIP (voice over internet protocol). Upstream provides direct relationship with worldwide communications providers, while PRISM connects that relationship via the FBI, a method to navigate through the USA’s own privacy laws.
This is where it gets interesting.
The above technology protocols fit with what was inserted into the New Zealand GCSB and TICS amendment bills, legislation that became law in 2013. (Ref. see my special investigation, TDB, Manning, August 18 2013).
The legislation empowered the state to command ISPs and Telcos to insert GCSB-controlled hardware into their networks.
Also, the legislation made it mandatory for ISPs and Telcos to inform the GCSB of, and enable the GCSB to test, any new technology (hardware or software) that may provide a degree of encryption that potentially pulled a curtain closed on the spies, rendering GCSB sniffer and filter window technologies unable to monitor our data and communications.
For those still skeptical about whether New Zealand has capability to monitor/filter through the use of technology huge data-flows to and from New Zealand, consider this: New Zealand’s Department of Internal Affairs already sniffs and filters data in its attempts to warn off people who accidentally, or otherwise, access objectionable and disturbing material on the internet.
Online users who do stumble on such material are presented with a Department of Internal Affairs page that displays on their computer screen stating that they have been blocked from accessing a website. The message states the reasons for DIA to have blocked access. The move is obviously in the public good and has generally been supported by the public.
So sniffer capability is already in evidence. Storage or management of huge amounts of data, for the purpose of surveillance, is another matter.

WHAT’S ALL THIS ABOUT METADATA THEN?
Metadata is the tip of the surveillance iceberg. As Edward Snowden said on Monday night, metadata is an analyst’s dream as it doesn’t lie. It shows who a person talked to, the time, the location, the duration. It can easily be cross referenced and applied layer upon layer. It can be visually analysed, geospatial analysis can be used to identify patterns of connections between disparate groups, cells, networks, individuals. This data is powerful.
Back to Xkeyscore.
XKeyScore acquires your information via DNI Upstream sensor sites (which Snowden referred to as being located in Auckland and Northland) and pre-positioned access points at ISPs (a capability that the GCSB and TICS legislation made lawful and asserted a requirement obligation on the country’s ISPs).
The principle of mass surveillance is a matter of definition. What governments define as surveillance is often quite different to how you or I may define the word.
But for the purpose of this piece, surveillance – whether it be technology-driven dragnet ‘indiscriminate’ surveillance, or human analyst driven search surveillance – it is one of the same. It involves four elements: Trafficthief (metadata), Pinwale, MARINA, and the big foundation of the four: XKeyScore.
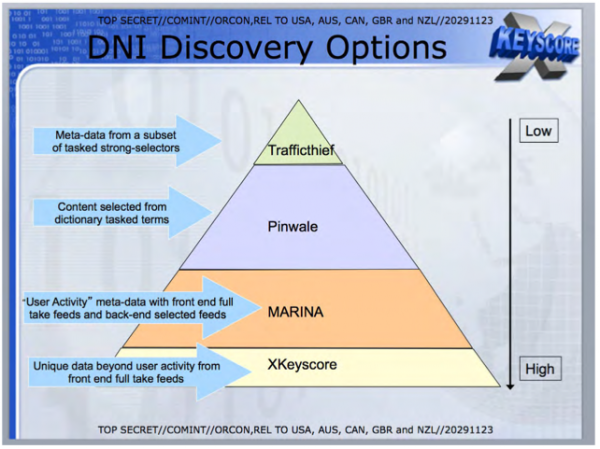
Remember too that with the help of Microsoft, the NSA stated in the source documents that it can easily crack high encryption. It also is able to decipher voice over internet protocol (VOIP) data calls on Skype (something that initially proved tricky).
THE INTERACTION BETWEEN GOVERNMENT BODIES:
Another important aspect to realise is how the NSA shares, cooperates, and utilizes the multiple jurisdictions permitted within separate departments of government.
Crossover and sharing of information is one thing, but sharing capability is the foundation of the relationship between intelligence agencies and the major estates of government.
We realised this to a degree in 2013 when it became known that the New Zealand GCSB was acting unlawfully when assisting the New Zealand Police to surveil Kim Dotcom. It also came to pass that 88 other New Zealand citizens or residents had also been unlawfully surveilled, although the circumstances of those offences were never revealed.
Let’s consider SIGINT (or signals intelligence). SIGINT developed as a primary tool of defence and military when acquiring intelligence on an enemy. But the NSA documents reveal SIGINT is vital to its ‘indiscriminate’ surveillance operations against the citizenry. Here in New Zealand, until recent times, the GCSB’s primary skill was signals-based.
The relationship between defence SIGINT activity and the NSA’s surveillance of the world’s citizens may also give some clarity as to whether the NSA does have a sensor site in Auckland and Northland. New Zealand Defence facilities are located here. And New Zealand Defence has an intelligence unit near Takapuna.
THE SIGINT DEFENCE CRYPTOLOGIC PLATFORM:
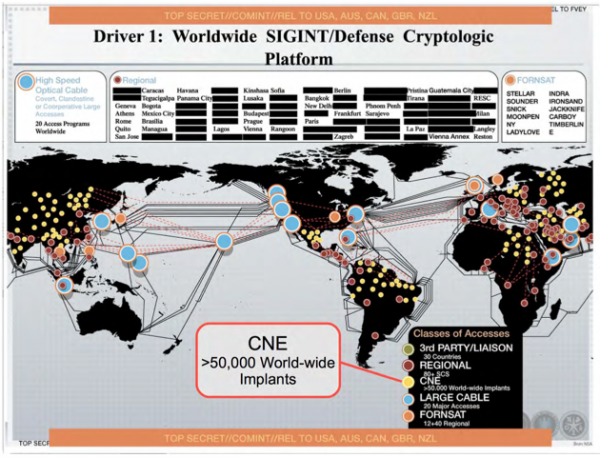
We know from the NSA’s own documents that the National Security Agency/Central Security Service shares “technological developments, cryptologic capabilities, software and resources for state-of-the-art collection, processing and analytical efforts, and IA capabilities.”
The intelligence exchange with Canada for example “covers national and transnational targets. No Consolidated Cryptologic Program (CCP) money is allocated to CSEC (Canada’s Communications Security Establishment Canada), but NSA at times pays R&D and technology costs on shared projects with CSEC.”
It has long been a question that remains unanswered as to whether New Zealand has received money to assist its spying for the Five Eyes Intelligence Agency. The Canadian experience suggests that at least in part, New Zealand has.
Some may ask, why would sovereign states like New Zealand, with a history of independent foreign policy give so much control away to a foreign superpower?
So what does the Five Eyes Intelligence Agency offer? Well, the NSA states the answer as: “… resources for advanced collection, processing and analysis” and open sharing of information/intelligence gathered via “covert sites at the request of NSA”.
In return, the Five Eyes member states provide the NSA “unique geographic access to areas unavailable to the U.S.”. (Ref. NoPlaceToHide Greenwald/Snowden doc: Page 121).
The NSA documents also state “comprehensive cooperation” is provided to ‘first tier’ member states Australia, Canada, New Zealand and the United Kingdom. While “focused cooperation” is exchanged with Austria, Belgium, Czech Republic, Denmark, Germany, Greece, Hungary and 13 other nations.
GEOGRAPHICAL REGIONAL SIGNIFICANCE:
 While the United States is able to reach and breach information on a global scale, its partners of the Five Eyes Intelligence Agency are valuable in part due to their location and geopolitical idiosyncrasies. Each has a unique opportunity capability.
While the United States is able to reach and breach information on a global scale, its partners of the Five Eyes Intelligence Agency are valuable in part due to their location and geopolitical idiosyncrasies. Each has a unique opportunity capability.
The NSA documents show that Australia’s location and interactivity with Indonesia assists the NSA to target “high priority targets” inside Indonesia.
While it is yet to be clear what New Zealand provides the NSA in terms of international trading partner intelligence, New Zealand’s relationship and trading status with the People’s Republic of China provides a specific and unique trade-led environment that others, including the USA, do not share.
Also, New Zealand’s capital city Wellington is the location of a significant French diplo-contingent. The French Embassy in Wellington is the fourth largest of France’s foreign affairs posts and interconnects with France’s territories in Polynesia and French Polynesia. This includes its need to assist in the transit of its military hardware in the wider Pacific basin.
New Zealand’s external offshore signals surveillance, via the GCSB base at Waihopai, is now well known. What is not so well appreciated is that the GCSB’s patch is east of Australia’s east coast, northward and eastward then out into Polynesia and French Polynesia. It would seem likely that China aside, France’s interests in the Pacific are the target of New Zealand Government spying.
SO WHAT HAPPENS TO ALL THIS INFORMATION?
So where does this intelligence all end up?
What kind of personal information is gathered?
The NSA documents show us that virtually everything is acquired.
Internet surfing, webmail (Yahoo, Hotmail, Gmail etc), Facebook, Myspace etc, internet searching (Google, Bing, Wikipedia etc), online mapping (Google Maps, Mapquest etc).
Xkeyscore and a number of other platforms collect all forms of communications. To cite the NSA: “Communications, day to day activities, contacts and social networks, photographs, videos, personal information (e.g. addresses, phone, email addresses), location and travel information.”
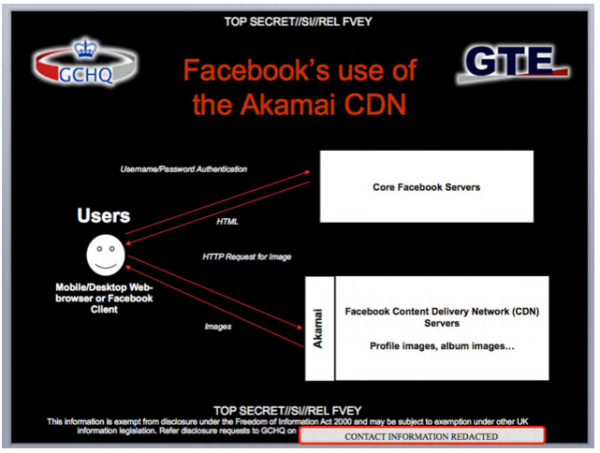
Facebook, Myspace, Bebo, and now Kik, Instagram, Twitter and a host of other social media platforms provide the NSA “A very rich source of information on targets: personal details, pattern of life, connections and associates, media,” the NSA documents state.
And social media friends… if you think Facebook’s lockdown security settings provide you with privacy, think again. The NSA’s ‘Passive’ system enables this global system: “the opportunity to collect this information by exploiting inherent weaknesses in Facebook’s security model.”
Also, at the time the NSA documents were acquired, the Five Eyes alliance was advancing its capability to track and monitor the communications of passengers of aircraft.
The UK’s GCHQ was leading this breakthrough technology. This new system referred to as Thieving Magpie hacks into any GSM and GPRS calls and data communications emitting form onboard aircraft. It is able to probe such communications every two seconds, while the aircraft is flying anywhere in the world.
In 2013 the NSA documents noted that “many airlines are offering on-board mobile phone services, particularly for long haul and business class (list is growing).”
Thieving Magpie was anticipated to provide XKeyScore “global coverage” via its Southwinds platform at some stage in 2014.
This technology announcement was provided to all Five Eyes member agencies, including New Zealand’s GCSB.
Of course, the New Zealand National-led Government has not informed its citizenry of any of this information.
The GCSB was informed that once Thieving Magpie’s global capability is achieved it will be “available to FVEY (Five Eyes) users” via a simple to use “light weight web page”.
THE SINISTER SIDE OF OUR SPYS’ METHODS:
Disturbingly, the NSA documents indicate how the use of sinister manipulation can destroy the reputations of Five Eyes targets, the NSA documents also describe how “radicalizers appear to be particularly vulnerable in the area of authority when their private and public behaviors are not consistent.
It lists four behaviors to look out for when surveilling a target, to identify the:
- “Viewing sexually explicit material online or using sexually explicit persuasive language when communicating with inexperienced young girls;
- Using a portion of the donations they are receiving from the susceptible pool to defray their own personal expenses;
- Charging an exorbitant amount of money for their speaking fees and being singularly attracted by opportunities to increase their status; or
- Being know to base their public messaging on questionable sources or using language that is contradictory in nature, leaving them open to credibility challenges.”
It is important to note here that the term radicalizer, does not mean criminal, but rather refers to a person who has become a target, whose political thinking does not knit well with those of the governments connected to the Five Eyes intelligence agency.
This method of attack the messenger, or ‘radicalizer’ as is defined by Britain’s GCHQ in the briefing documents, conveys a four-point-plan of character assassination: Deny, Disrupt, Degrade, Deceive. Known as ‘The Four Ds’.
How the Four Ds are used are detailed:
- “Set up a honey-trap
- Change their photos on social networking sites
- Write a blog purporting to be one of their victims
- Email/text their colleagues, neighbors, friends etc.”

This information was presented by the NSA to New Zealand’s GCSB officers in a training/briefing session.
The NSA officer briefing the Five Eyes spies added: “Honey-trap; a great option. Very successful when it works. Get someone to go somewhere on the internet, or a physical location to be met by a ‘friendly face’. JTRIG has the ability to ‘shape’ the environment on occasions.”
The officer adds that changing a person’s photograph on a social media profile page is effective in driving up paranoia: “Can take paranoia to a whole new level.”
And the officer suggests email and txt operations can assist the state’s spies to gain credibility with online groups and infiltration of the same.
The above methods will no doubt ‘ring a few bells’ and cause some unease for New Zealanders who have become privy to the inner workings of Dirty Politics, as practiced by members of the National Party and their attack merchants in the blogosphere and media.
And in case the connection still needs accentuating, here is a direct quote from the NSA briefing to the New Zealand GCSB: “Issues of trust and reputation are important when considering the validity and appeal of the message. It stands to reason that exploiting vulnerabilities of character, credibility, or both, of the radicalizer and his message could be enhanced by an understanding of the vehicles he uses to disseminate his message to the susceptible pool of people and where he is vulnerable in terms of access.”
If the messenger or target ‘radicalizer’ needs to be shut down, the NSA advice is to “Bombard their phone with text messages, bombard their phone with calls, delete their online presence, block up their fax machine.”
If a computer or site or network needs to be taken down, the officer also said: “Send them a virus: Ambassadors reception – encrypt itself, delete all emails, encrypt all files, make the screen shake, no more log on. Conduct a denial of service attack on their computer…”
According to the NSA documents, ‘Effects Operations’ save time and money when compared to “traditional law enforcement”.
And in a section titled: DISRUPTION Operational Playbook, it breaks it down into easy-to-follow terminology:
- Infiltration Operation<
- Ruse Operation
- Set Piece Operation
- False Flag Operation
- False Rescue Operation
- Disruption Operation
- Sting Operation.
Remember all of the above methods do not require the targets to be terrorists, sympathisers, or criminals, but rather ‘radicalizers’ which in New Zealand’s context appears to mean opposition politics, civil society spokespersons, academics, activists, and independently minded and branded journalists (investigative or otherwise).
CONCLUSION:
It is clear that paranoia and fear are being underlined as effective methods to be used to destroy those who voice opposition to the expressed orthodoxy or policies advanced by Five Eyes governments.
Being informed is being forewarned.
This investigative report is syndicated by MIL OSI and was first published on LiveNews.co.nz
—







I once worked in the late 90s for a US IT firm. Here they worked on health systems and payrolls but different divisions in Australia and US worked on top secret combat systems for submarines and naval ships.
None the less all outside internet and email traffic was routed over private leased lines to their computer centre in Crystal City, a suburb near the Pentagon in Washington DC. This is how they protected their secrets ( from going out) and cyber attacks coming in. First you had to penetrate a very secure constantly supervised entry point. I cant imagine they are any less secure 15 years later.
And this is how you do cyber security for leading firms in NZ, make sure there is only one entry point into a company WAN.
Thank you for this very timely and extensive analysis of their capabilities and modus operandi.
Coincidentally, this op ed from James Bamford just appeared in the NYT (http://www.nytimes.com/2014/09/17/opinion/israels-nsa-scandal.html?emc=edit_th_20140917&nl=todaysheadlines&nlid=15599012) revealing the end result of the data dragnet: how it is used against real people in the real world of the NSA’s friends and foes. (Not saying America here, because I think there’s a big difference between the NSA and what Americans ever voted for or knew about).
Here are the opening paragraphs, hopefully enough to get people to read the whole item, and think:
***********************
In Moscow this summer, while reporting a story for Wired magazine, I had the rare opportunity to hang out for three days with Edward J. Snowden. It gave me a chance to get a deeper understanding of who he is and why, as a National Security Agency contractor, he took the momentous step of leaking hundreds of thousands of classified documents.
Among his most shocking discoveries, he told me, was the fact that the N.S.A. was routinely passing along the private communications of Americans to a large and very secretive Israeli military organization known as Unit 8200. This transfer of intercepts, he said, included the contents of the communications as well as metadata such as who was calling whom.
Typically, when such sensitive information is transferred to another country, it would first be “minimized,” meaning that names and other personally identifiable information would be removed. But when sharing with Israel, the N.S.A. evidently did not ensure that the data was modified in this way.
Mr. Snowden stressed that the transfer of intercepts to Israel contained the communications — email as well as phone calls — of countless Arab- and Palestinian-Americans whose relatives in Israel and the Palestinian territories could become targets based on the communications. “I think that’s amazing,” he told me. “It’s one of the biggest abuses we’ve seen.”
It appears that Mr. Snowden’s fears were warranted. Last week, 43 veterans of Unit 8200 — many still serving in the reserves — accused the organization of startling abuses.
In a letter to their commanders, to Prime Minister Benjamin Netanyahu and to the head of the Israeli army, they charged that Israel used information collected against innocent Palestinians for “political persecution.”
In testimonies and interviews given to the media, they specified that data were gathered on Palestinians’ sexual orientations, infidelities, money problems, family medical conditions and other private matters that could be used to coerce Palestinians into becoming collaborators or create divisions in their society.
****************************
Could such tactics explain the otherwise very puzzling behaviour of certain New Zealand politicians and media? Just an idle thought.
The use of data collected by the NSA for blackmail is one of the subjects discussed by NSA whistleblower Russ Tice.
This is what the Israelis caught up in the Christchurch earthquake were up to. Spying on local palestinians is their main function but having an embassy spybase in Wellington helps them keep electronic eavesdropping on government officials and Mps
Wow Selwyn. This must have been a mammoth effort to put together.
Now that’s Journalism! Awesome. Such a good informative read.
Are you expecting to be denied internet access anytime soon?
Needs to be front page MSM.
We are onto you – you GCSB freaks, and you grubby, grubby, dirty Treasonish National govt.
FJK and all his cronies.
Opinion and belief.
Well done Selwyn, very well laid out and coherently presented. Seems perfectly logical that you would have private limited liability companies contracted to provide your data collection services and it’s win win for them, they have guaranteed payment on their monthly invoices and the opportunities for insider trading must be as vast as the metadata they collect. Not being subject to OIA requests must have inherent advantages as well I imagine?
Exactly. The essence of every PPP is that they combine all the powers of government with all the freedoms enjoyed by the “citizens” that are corporations.
What one can’t do, the other can. What restrains one is evaded by the other.
A PPP is a two-fisted blow to democracy.
Great comment! Just as the spy agencies set up shop in different countries to be able to “collect it all” because of different legal systems, the spy agencies are using different corporate laws to be able to spy on us all.
And the causality is democracy which requires privacy
Can’t really say anything here, I know I’m being watched f#%$@#*&
Thankyou Selwyn for this excellent synthesis of the bigger picture regarding Snowdens revelations into a slightly smaller chunk. You highlight well some of the many almost outright fascist tactics that seem to have become perfectly acceptable tradecraft of modern “Intelligence Professionals” that we trust to uphold democracy in our Countries. One can only hope that privately there are many others apart from those in Israel’s unit 8200, ie in our 5 eyes agencies here and abroad who still posess a conscience,compassion and a desire to uphold the values that some of our family members sacrificed lives or sanity for while fighting WW2. Let’s hope also that some of those people are quitely doing their best behind the scenes to fight the excesses of this emerging totaliarian global system of control, in their own measured ways.
The problem with the sheer complexity of much of the information and all the jargon is that it puts people off investing even a small amount of their precious time into digesting its meaning and impact properly. Also there is the tendency for even outright denial of what is ostensibly very difficult realities to accept emotionally. It is scary, and people have a right to feel anxiety when thinking about what such a system of complete control could be used for by unethical leaders who could rise to power in any one of our countries without warning at a future time.
We need to inform others of this information and vote with our hearts not just our heads.
I’d like to know who makes all the profit off our money every night when all our banking transactions are sent over this cable to other countries.
And I want to know why the banks send our money overseas every night, when the money isn’t there’s in the first place – it’s ours – and someone who is not us is making money off it!.
Well thats exactly what you get with foreign-owned banks.
The answer is quite simple: Transfer your money to a NZ-owned and operated bank.
If every one did this, then the problem would disappear.
Is Kiwibank NZ owned?
ALL banks undertake this practice – NZ banks and foreign banks. ALL BANKS!
Opinion.
The banks are nett borrowers. There is nothing to send off ‘overnight’
The NZ state isn’t sovereign.
At the deep state level NZ has no independent foreign policy, since NZ’s commander in chief is a foreigner. This issue is highlighted by the difference between the policy of the NZ military in Afghanistan and the policy of the NZ state executive as decrived in Hager’s “Other People’s Wars”.
NZ govt are allowing these gross inhumanities of war – as part of the 5 eyes spy network.
Cut the cable now!!!!!!
Opinion.
What do you think of Ms Gwyn coming to Key’s aid today by saying;
“I see no evidence that the GCSB has been engaged in mass surveillance”?
Was this statement by Ms Gwyn wrongly quoted by someone who does not have the advanced knowledge that you have bought together?
If so can we forward to her as evidence that there is a certain proof that planned surveillance is occurring and will she now investigate this issue properly?
Your excellent work here must be put to the public good thanks to you.
I think 30 pieces of silver ….that’s what I think.
All its all a charade about the IG anyway.
The law allows him to write a ‘certificate’ to allow GCSB to hide anything from IG.
They tried a version of this when Bill English signed a certificate to prevent the knowledge of GCSB coming out in court over spying on KDC.
But KDC lawyer was too clever and got the evidence ‘they were in the room’ from a police inpsector in the witness box
Co-Location
Front running
CFH UFB
GCSB
SIS
Peter Thiel
John Key
Palantir
Facebook
PayPal
Xero
http://www.nzherald.co.nz/business/news/article.cfm?c_id=3&objectid=10702787
I just watched the sliver of last night’s debate presented by the Herald. What I have to say is that the moderator talked over the top of Cunliffe’s response on the spying issue, then switched immediately to the numbers. Cunliffe only managed to get in one word – “privacy”.
Given the importance of the issue, this was terrible behavior on the part of the moderator. I suppose the Herald is to be commended for highlighting this moment. However, Cunliffe used precious time cosying up to Key when he should have been distancing himself. Not good. The issue is far too grave.
The only reason those companies operate in NZ is because Key signed off on it with the GCSB, right? He has given them permission to access Kiwi metadata via XKeyscore, which is unable to be tracked. So, Cheryl Gwyn can`t see a bloody thing, and will report that the GCSB are clean. Well, of course they are, Key knows that already. Great post – my take today here, NZ cannot uphold the law by breaking the law http://bit.ly/1r9GX50
I see kittens . I see little fluffy kittens playing with butterflies on a warm green meadow . Lalalalalala lalalala ……..
Fantastic effort Selwyn Manning . Thank you .
It would seem to me that we may as well elect a small bucket full of common garden snails to be our government and their similarities to our current crop of politicians is remarkable .
[…] Degree wasn’t journalism last night – this is journalism. To think in the wake of NSA spying revelations and Key’s privatisation of mass surveillance […]
The ‘steak’ is tainted beyond most people’s ability to even begin to get heads round. Three more years of it unthinkable
Feel totally sick but thankyou so much Selwyn. So many things this year here make awful sense now.
Wondered which real journalists Glen was working with. This should be headline and Key in cuffs. We do owe Kim Dotcom a debt of gratitude too.
Kim Dotcom is a black hat pretending to be white. To think he is some kind of evangelist for privacy is delusional. He had no interest in personal data freedom until it became convenient for him to do so.
He certainly didn’t care about the privacy of the employees at the companies he sold PBX entry codes to.
I used MegaUpload when it was live for years. I knew it was illegal, as does he.
> Abuse of power, and then denial. I see he is up for exactly the same charges he is claiming of John Key?
Interesting Markus,
You were happy to partake in what YOU believed to be illegal because it was convenient and you acuse Dotcom of wearing some kind of non coloured hat, dismissing what he believed. Mr Dotcom has not only the NZ State but also the US interests against him. Who does Key have to answer for his abuse of power giving that it may well be to the detriment of every NZ citizen?
@David.
Now that Kim.com has used his mind to reveal our govt skullduggeries, we can make key and his cronies accountable by voting for a CHANGE in govt on Saturday!
FJK! And F his crony dirt-dealing mates!
Change the govt on Saturday, and FJK will be held to account for his sellingout of NZ.
God Defend New Zealand!
Opinion.
[…] Here is an investigative report I published today that maps out the intelligence conundrum facing New Zealand. It suggests that […]
[…] Here is an investigative report I published today that maps out the intelligence conundrum facing New Zealand. It suggests that […]
Good Selwyn,
Let’s not play with semantics. If all of our data is collected and I believe it is being collected then does it matter who is doing it?
When these agencies use algorythems to identify any communication of interest to them does this then mean we are then being surveilled?
Of course not, we were already being surveilled for that data to be present. Nothing to hide, nothing to fear? so this presumes you know what they are looking for, does it not, todays laws can change (under urgency) tommorrow. Does key know all of this, maybe maybe not, he is simply the enabler, a traitor in my view. The first requirement of effecting any change is to first accept the situation. We are all being monitored, so why? I have and wrote a number of articles on this at the time of the law changes and clearly stated that the GSCB and other agencies are not to protect people but to protect the State FROM the people. What State though? because this presumes that the Various partner States have control over these agencies. An example, lets travel back a few years and consider myself and a number of other people still capable of independent thought trying to organise the demise of Hitler, in the greater good of course, would that State having these agencies capabilities use them to thwart that attempt? As Mr key would say I leave you to draw your own conclusions. We know he would.
Below is a link to 10 x approx 1.5 hr video seminars that I believe are not only intriguing, disturbing and surprising they also answer many questions historically and present day of the over all picture. If you don’t believe in religion and blame it for almost all our wars you would be wrong, it’s the cause of all our wars and you
really need to watch, I found it well worth the time investment. Maybe watch number 3 and 4 and if that piques your interest then watch them all, what follows is the shortened version.
http://walterveith.com/walter-veith-total-onslaught-mini-series.html
Following that path of thought, what proposed law change that you can imagine could land average New Zealander calling their mum and buying holden’s on trademe in trouble with the powers that be?
Is your issue with the law’s or the possibility to enforce them completely effectively via the data collected?
We see this logic commonly in the debate about speed camera’s. We all agree the roads should be safe, and need a speed limit, therefore we need laws, which require policing. Speed camera’s are an effective way of doing this. Supposing that speed camera’s didn’t involve fines, but arrests instead, is their any appeal to logic that the entire roading network shouldn’t be monitored for speeding 24/7?
The strawman approach…
You might be happy to forgo privacy, I am not. That is the debate the country was denied not to mention the debate about what the actual law changes enabled.
Excuse spelling and grammer i.e algorithms, tomorrow etc
‘Palantir’ is of course the name of the ‘seeing stones’ from Tolkien’s Middle-Earth writings. According to Tolkein himself, in the section on Palantiri in ‘Unfinished Tales’:
“Alone the Palantiri could only see: they did not transmit sound. Ungoverned by a directing mind they were wayward, and their visions were (apparently at least) haphazard. …. what they ‘saw’ was directed or hidden by chance, by darkness or by ‘shrouding’. The vision of the Palantiri was not ‘blinded’ or ‘occluded’ by physical obsticles, but only by darkess. …..
“A viewer could by his will cause the vision of the Stone to concentrate on some point. …. Controlled by the will of a skilled and strong surveyor, remoter things could be enlarged, brought as it were nearer and clearer, while their background was suppressed. … Great concentration might even enlarge some detail that interested the surveyor, so that it could be seen (for instance) if he had a ring on his hand.
“But this concentration was very tiring and might become exhausting. Consequently it was only undertaken when information was urgently desired, and chance (aided by other information maybe) enabled the surveyor to pick out items (significant for him and his immediate concern) from the welter of the Stone’s visions.
“The Palantiri could not themselves survey men’s minds, at unaware or unwilling; for the transference of thought depended on the wills if the user on either side, and thought (received as speech) was only transmittable by one Stone to another in accord.”
“Unfinished Tales,” p.530-1
Sounds a pretty good description of mass surveillance to me.
The best hiding place is always in plain view!
Happily….we all know what happened to Mordor in the end….
As we will see this Saturday 20th September.
This is the first thing I thought of when I read this excellent article. It reminded me of the quote in one of the LOTR movies: “A Palantir is a dangerous tool Saruman….we don’t know who else may be watching”. Well, now we know don’t we 🙂
Excellent, and quite frightening post, Selwyn Manning – thank you!
It should not be forgotten that the Pan Pacific Trade Agreement offers more of the same.
FJK may well have succeeded in sneaking this lot past us, by lying and deceit and trickery.
We MUST ensure that he does not succeed in pulling the wool over our eyes again by doing more (and similar) damage to the country disguised, this time, as a “Free Trade” agreement.
People don’t like being manipulated. Yet the people of this country have clearly been well-and-truly manipulated by this pack of idiots.
Depressing to hear some of the views expressed by ‘the man or woman in the street’ on RadioNZ this morning –
“Only those with something to hide would be worried by this.”
“It’s what Governments do, don’t they?’
“Baaaa, Baaaaa, Baaaaa.”
&tc.
“Eternal vigilance is the price of liberty—power is ever stealing from the many to the few…. The hand entrusted with power becomes … the necessary enemy of the people. Only by continual oversight can the democrat in office be prevented from hardening into a despot: only by unintermitted Agitation can a people be kept sufficiently awake to principle not to let liberty be smothered in material prosperity.” –
Wendell Phillips, speech in Boston, Massachusetts, January 28, 1852.
“Dear God! the very houses seem asleep;” –
William Wordsworth, ‘Composed upon Westminster Bridge, Sept. 3, 1802″
“Beam me up, Scotty.” –
James Tiberius Kirk, various.
So are there any radicalizers out there who can report something like this happening to them?
I don’t consider myself a radicalizer by any means, but have been a victim of unjustified surveillance of my webmail, interference with my cellphone and my partners, and have had hacking attempts made against my systems from most likely a foreign government agency.
I’m not a protestor,agitator, or criminal and I don’t make threats against anyone online but presumably one of my friends said something stupid online and I got brought in to the dragnet. Intelligence agencies are supposed to practise discrimination so as not to waste precious resources on non-threats but I guess anything goes these days post 911. I also have a friend who claims to have been hacked by IP ranges that connect to .mil.nz domains, although I have not seen his technical evidence personally. In his case he had the ‘temerity’ to simply speak out about illegal surveillance both here and abroad on his twitter feed and then the attacks started after that. He has been under considerable emotional distress after discovering that he was being repeatedly attacked and his windows based systems ruined at a hardware level, to the extent he felt cause to sell his home and move location. He works as a systems support administrator in a high level company so knows his stuff also.
My vodafone based webmail was intercepted by man-in-the-middle SSL certificate substitution, which I discovered by checking the technical parameters one day when traffic to my pc was slow. The dates expiry on the SSL certificate were contradictory which was the first giveaway. I then installed and used the “perspectives” certificate checking addon for firefox web browser, and used this to study the SSL certs granted to my connection from different ISPs. The bad certs continued for several months then mysteriously stopped. There have been a couple of times this year when it happened again briefly.
My cellphone used to have regular echo seemingly mixed into my voice calls whenever I was talking to someone I had a personal connection with about 2 years ago. It happened repeatedly, and was not a glitch as all cellphones and cell tower base stations have had realtime digital software code in operation for years that cancels virtually all latency based echo. The type of echo I had was maybe around 500 milliseconds, and made it near impossible to talk. I presume it was an attempt to intimidate me and measure my pschological response, etc. Naturally I tried calling vodafone for assistance but they were not able to help, other than offering typical reboot your phone advice and doing some diagnostics on my ‘line’ which came out fine. I don’t use a smartphone either.
My partners old phone turned out to have a rare feature in it’s firmware, that could alert the user if the GSM A5 encryption was not in operation during a call. A small unlocked padlock icon would appear on the screen during the call. The was not related to web-page SSL encryption as it was not a smartphone nor configured for WAP access. I searched in the manual and found a very brief reference to the no encryption alerting feature buried near the back in the help section. I then did more research online and found that there are just a handfull of models in the world that do report this type of connection failure, and by pure luck my partners was one of them. All GSM calls are meant to be encrypted by default with the A5 algorhythm and when they are not it’s usually a sign that you have been bumped onto an illegal basestation or portable interception rig, which are now available in a suitcase formfactor for huge sums of money. I have no doubt that there may be foreign spies in our country with such gear or else the police are using them additionally to the legal intercept capability that the GCSB and Telco’s have at exchanges and in cellular basestation – “home location registers”. The location where my partner lived at the time is quite near a foreign embassy for a certain middle eastern country, which might just be a causative factor for this isolated incident alone. I wrote vodafone a long technical email explaining my evidence that one of their basestations had been hacked and was told by the CSR that the one in question was under maintenance “for an upgrade”. Plausible Deniability in action I guess…
The most obvious hacking attempts against my PC systems were of two types primarily. The first consisted of unusual DNS (Domain Name Server) reply packets from what appeared to be an internal IP address behind my router, but on closer inspection were from an unsual IP (designed to look look a non-routable address) connected with the AINET autonomous system network based in Maryland, USA. I had been running a packet capture analyzer called wireshark that day so had picked them up by pure chance while looking at regular traffic. This type of malformed DNS reply is typically used to push a web browser to load a website from a different server masquerading as a legitimate one, and is one of the techniques that was exposed in the Snowden material. From there customised exploits aimed at infecting a host system based upon web browser version and current software bugs are able to be deployed as a return payload. Rather than fix this directly, I opted for changing OS altogether at the time.
The second type of attack was with redirected traffic from a Facebook Ireland associated CDN server that was issuing brief port scans against my external IP address and home ADSL connection. I later found evidence with wireshark of the same type of activity against my partners PC via her cellular internet based connection on a different ISP. There are murmerings within the Snowden/Greenwald documents of fake facebook servers being used as an NSA attack platform, so I doubt that the incidents I have explained are from underground hackers.
Sorry to overwhelm readers with technical details but there is only so much that can be explained simply. My intention in typing all this out carefully is not to make intelligence gathering difficult or exposed to undue scrutiny, but to illustrate to others that it does actually happen. I am upset that I have been targetted in this way and that there is no legal recourse for me to fight against it, along with no means to stop it occuring again! It is undemocratic in the extreme that there is no way we can make things right or ‘come clean’ to an intelligence agency when we have been unfairly harrassed and targetted as I,my Partner, my Friends and presumably my Family have been. Why is there no means available for contact? Why can we not be interviewed about our lives privately to clear up any concerns? I would happily take a lie detector interview to stop the harrasment but there is simply no mechanism for people to do so unless they are applying for a security clearance which obviously I won’t be. The whole situation is utterly reprehensible when you are a victim of unjustified, unwarranted and most likely – illegal surveillance and psychological harrassment as I believe myself to be…
I’m no apologist for Key or his government but we are pawns in the game – previous governments went along with NSA requirements and future governments will do so too – listening to Cunilif this morning on how he would deal to this it was apparent that it would be business as usual.
Here’s what happens when one tries to buck it:
http://www.theguardian.com/world/2014/sep/11/yahoo-nsa-lawsuit-documents-fine-user-data-refusal
And here’s where much of the data is stored”
http://en.wikipedia.org/wiki/Utah_Data_Center
It’s quite possible to stop all this, but we have to get rid of the complacency that maintains the situation as it is, and permits it to persist in the encroachment aspect. After that, we need to get organised, because the competition is.
So, will it happen? No, of course not. Everybody isn’t feeling enough pain. The human animal doesn’t seem to possess the brain to understand that a stitch in time saves blood up to the height of the horses bridles further down the track.
Well, they do, but they’re comfortably numb, and content to be herded like … sheep, into the category of ‘production unit’, with that box in the suburbs, basic health care, which makes economic sense when weighed up against retraining cost, and just enough money allotted for effort involved to enable us to purchase a sufficient quantity of the products we make in earning it, to cover production overheads to finance the rest of the venture.
We have attributes; as a resource we are defined within the economic disciplines as ‘non-rivalrous’—we breed our own replacements at a faster rate than they can be employed—but, please try to be reasonable, we have to be open-minded here. How are the ones that employ us supposed to be able to run an efficient marketing aspect if they don’t have full access to all our personal information?
Not much , if any of what we’ve been witnessing of late might have come to pass without Kim Dotcom . Life is strange . And our bedfellows stranger still .
Our very democracy was dependent upon us using the gun and the bomb . The same kind of thing our enemies used . Isn’t that odd when you think about it ?
Done thinkin’ , now for drinkin’ . Dulls the irony .
“Google Acts Like Privatized NSA: WikiLeaks’ Julian Assange
In interviews with BBC and Sky News, WikiLeaks founder explains how Google’s behavior, though legal, is like that of surveillance agencies.”
article posted on the web. This goes beyond the PPP to a pure P play
Pee on the citizens? or P on the “citizens” to go along with PPP on “citizens”
http://www.commondreams.org/news/2014/09/19/google-acts-privatized-nsa-wikileaks-julian-assange
Comments are closed.